Microsoft now actively publishes backdoors found for the Exchange server breach, see the security blog here
You can download a csv file with the known filepaths, which are very easy first step to verify here
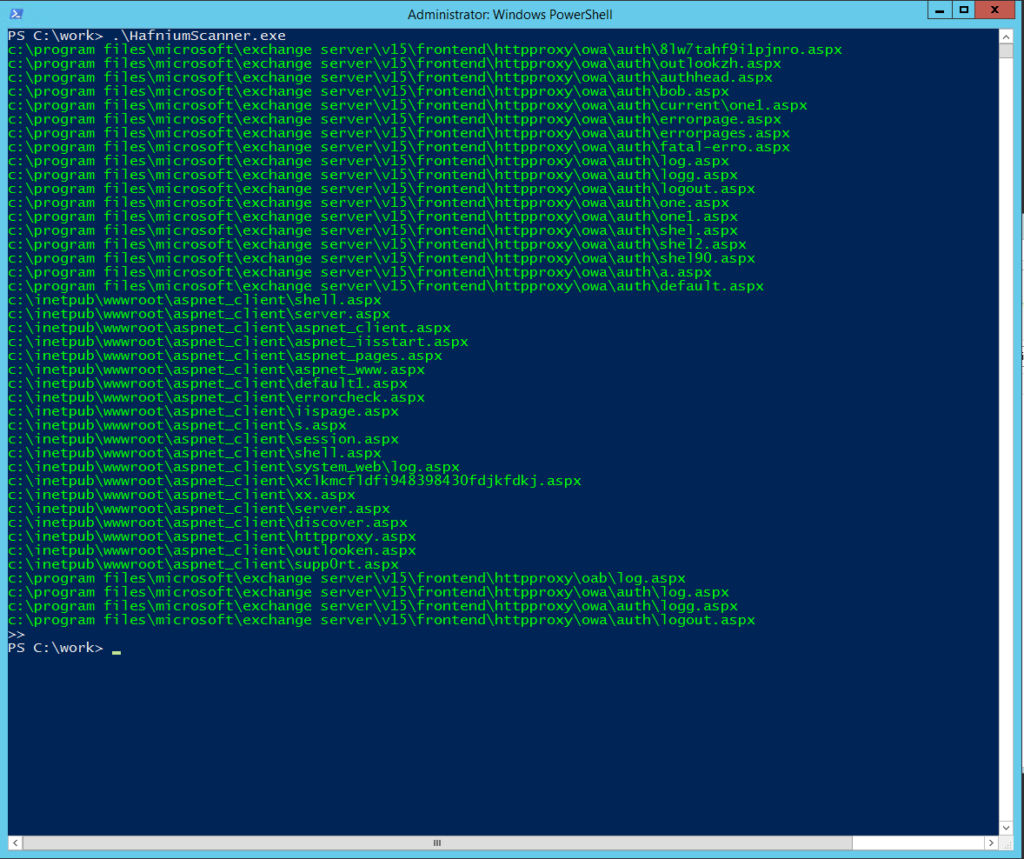
Below is a very quick first response program to use that file, and scan if a known backdoor is present on your system. Compile and run it, and it will simply check each entry on the list on your system to see if the file is present. Green means not found, good!. Red means a backdoor is present.
A single red line (or more..) means your system is compromised.
This is a first check only, and should by no means taken as a full detection, or beware – solution.
using System;
using System.IO;
namespace HafniumScanner
{
internal class Program
{
// set these to your values
private static readonly string DEFINE_INSTALL_DRIVE = @"c:\";
private static readonly string DEFINE_MS_CSVFILE = @"c:\work\attack.csv";
private static void Main(string[] args) {
var defaultcolor = Console.ForegroundColor;
var reader = new StreamReader(DEFINE_MS_CSVFILE);
while (!reader.EndOfStream) {
string buffer = reader.ReadLine();
string[] parms = buffer.Split(Convert.ToChar(","));
string filepath = parms[2].ToLower();
if (filepath.StartsWith(DEFINE_INSTALL_DRIVE)) {
if (File.Exists(filepath)) {
// red, backdoor is present
Console.ForegroundColor = ConsoleColor.Red;
Console.WriteLine(filepath);
}
else {
// green, not found
Console.ForegroundColor = ConsoleColor.Green;
Console.WriteLine(filepath);
}
}
}
Console.ForegroundColor = defaultcolor;
reader.Close();
Console.Write(">>");
Console.ReadLine();
}
}
}
There are many places where you can verify the md5 hash for this file online, it should read: F7F7D4CA554A59909159D0BE8D0600DD