The usual way visitors land on your SSL site, is by connecting to a normal HTTP version which perfoms a redirect to the SSL version of the website. This works great. By using strict transport security you can improve the security of your visitors further. It offers a method to tell the browser of the visitor to skip the HTTP version next time alltogether, and connect *only* using SSL with your domain. A correct configuration takes multiple steps, which you will need to follow closely. Not taking all required steps will break the chain of trust and render strict transport security ineffective.
- If you redirect multiple ‘catch names’, you need to redirect/upgrade them to SSL versions FIRST, before redirecting to the final SSL destination. mydomain.net -> SSL mydomain.net -> SSL mydomain.com
- Redirect from your HTTP site using the 301, not the default 303. (see first image below) mydomain.com -> SSL mydomain.com
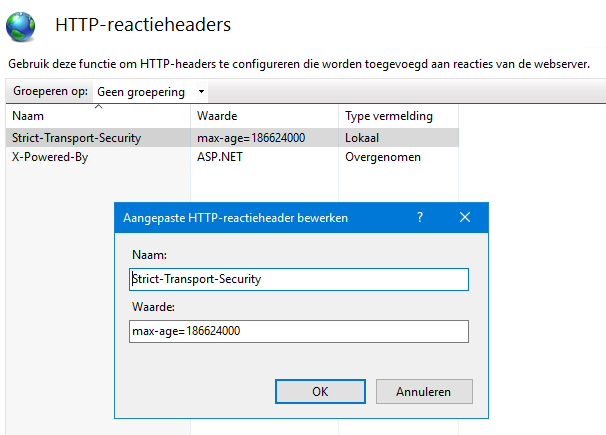
- Set an additional HTTP response header with the name ‘Strict Transport Security’ and your desired value in seconds, eg ‘31536000’ for one year. (duration in seconds). See the second image below.
Image1, Redirect using 301 status code
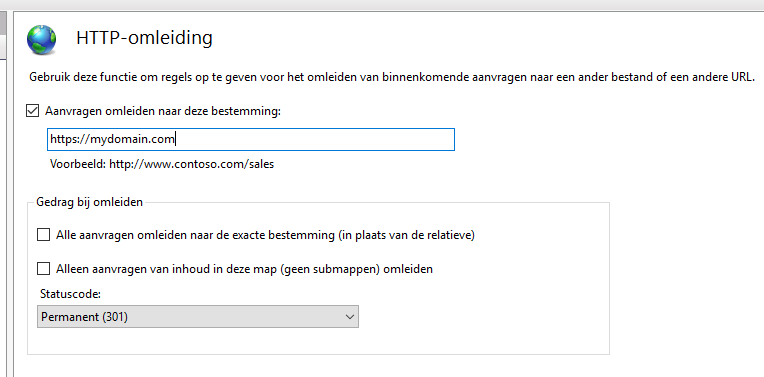
Image2, Set the additional header and duration in seconds